PHPF (New)
Read more at https://www.phpclasses.org/package/10204-PHP-Reformat-PHP-scripts-according-to-code-style.html
We are just over a couple of months into 2017 and I am seeing the gym motivation starting to quiet down. As veteran members all know the wait for gym equipment usually peters out by the beginning of February as most of the new members stop going to the gym or at least stop coming very often.
I always think of new years as being a very trendy time for gym memberships as the prices drop to get new members and there is a lot of excitement as many people show up for the first time and then get bored, sore and disillusioned and move on to the next exciting thing in their lives.
A few people we will see get the bug and do not stop and will become lifelong lifters but I always used to wonder what makes the difference between those that stay at the gym and those that leave.
Here is my list of the things that stop people from hitting the gym and how to get around them.
 1. No pain, no gain – The problem here is that most people push themselves far to hard and have no time to recover between workouts and after being sore for a month it is impossible to go on. This looks to newbies as a ridiculous lifestyle.
1. No pain, no gain – The problem here is that most people push themselves far to hard and have no time to recover between workouts and after being sore for a month it is impossible to go on. This looks to newbies as a ridiculous lifestyle.
To get away from this problem why not just slow down. If you want to look hot for the summer why not take it a little easier. The beach will still be empty next week so dont kill yourself trying to look like a greek god now.
2. No results – When getting started in a gym you may not get fast results in losing weight. Your workouts are going to lose you fat as well as gain you muscle so you are going to not be losing as fast as you hope.
Give it time.
As you gain muscle it takes your body more calories to keep that muscle, as well as increasing your metabolism, which in turn will help you lose fat.
3. Tiredness – This relates to number one. You will be tired as your body adjusts and as you gain strength, lose fat and get healthier. After you adjust to the new workouts you will get more energy and not be nearly as tired as you were before you started this healthier lifestyle.
4. No time except for the gym – This is a doozy. When you get started the only thing that matters is going to the gym and then suddenly you have lost touch with the rest of the world and you miss that.
Why not just start reducing the time you workout. You do not need to work out two hours a day. 45 minutes to an hour is all you should be spending in the gym as you get started.
5. Boredom – Boredom can definitely creep into your attitude at the gym. This is usually caused, I believe, from not having a plan, goals and a way to make sure that you are going to achieve them.

If you just go in and lift weights randomly or do a cardio workout when you cant think of any muscle groups that you feel like doing then you are quickly going to get bored and not know why you are spending time in the gym.
Get together with a trainer at the gym that you join and get a plan together for what you are going to do each day in the gym and set some realistic goals and you should be set.
Other than these issues the biggest issue is that the first gym you saw was the one you joined and you just might not enjoy working out there. Try going through my list of how to choose a gym, and my other gym staff articles to make sure that you pick the right place to workout and keep your gym motivation up.
Article source: http://www.fitnesstipsforlife.com/making-a-gym-work-out-for-you.html
Of the many, many, many bad things about passwords, you know what the worst is? Password rules.
If we don't solve the password problem for users in my lifetime I am gonna haunt you from beyond the grave as a ghost pic.twitter.com/Tf9EnwgoZv
— Jeff Atwood (@codinghorror) August 11, 2015
Let this pledge be duly noted on the permanent record of the Internet. I don't know if there's an afterlife, but I'll be finding out soon enough, and I plan to go out mad as hell.
The world is absolutely awash in terrible password rules:
But I don't need to tell you this. The more likely you are to use a truly random password generation tool, like us über-geeks are supposed to, the more likely you have suffered mightily – and daily – under this regime.
Have you seen the classic XKCD about passwords?
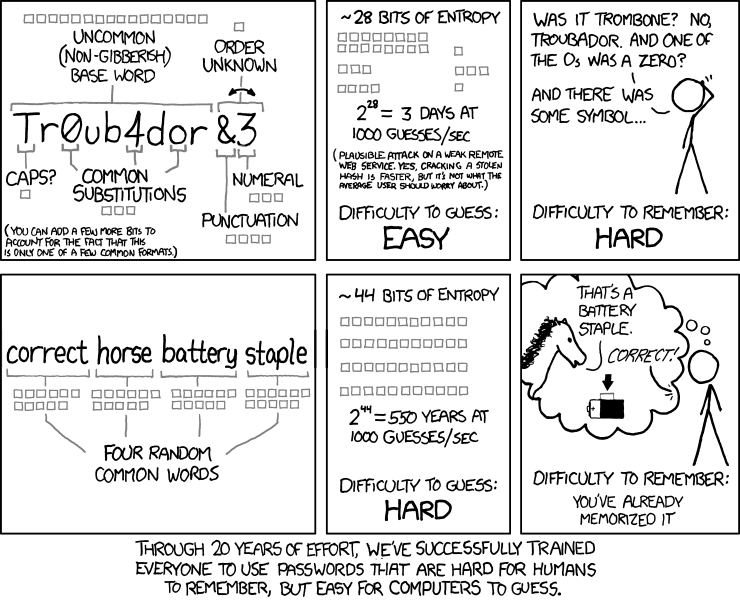
We can certainly debate whether "correct horse battery staple" is a viable password strategy or not, but the argument here is mostly that length matters.

No, seriously, it does. I'll go so far as to say your password is too damn short. These days, given the state of cloud computing and GPU password hash cracking, any password of 8 characters or less is perilously close to no password at all.
So then perhaps we have one rule, that passwords must not be short. A long password is much more likely to be secure than a short one … right?
What about this four character password?
What about this eight character password?
Or this (hypothetical, but all too real) seven character password?
@codinghorror I'm sorry but your password must contain 1 char each from: Arabic, Chinese, Thai, Korean, Klingon, Wingdings and an emoji
— Finley Creative (@FinleyCreative) March 3, 2016
You may also be surprised, if you paste the above four Unicode emojis into your favorite login dialog (go ahead – try it), to discover that it … isn't in fact four characters.
Oh dear.
"💩".length === 2
Our old pal Unicode strikes again.
As it turns out, even the simple rule that "your password must be of reasonable length" … ain't necessarily so. Particularly if we stop thinking like Ugly ASCII Americans.
And what of those nice, long passwords? Are they always secure?
aaaaaaaaaaaaaaaaaaa
0123456789012345689
passwordpassword
usernamepassword
Of course not, because have you met any users lately?

They consistently ruin every piece of software I've ever written. Yes, yes, I know you, Mr. or Ms. über-geek, know all about the concept of entropy. But expressing your love of entropy as terrible, idiosyncratic password rules …
… is a spectacular failure of imagination in a world of Unicode and Emoji.
As we built Discourse, I discovered that the login dialog was a remarkably complex piece of software, despite its surface simplicity. The primary password rule we used was also the simplest one: length. Since I wrote that, we've already increased our minimum password default length from 8 to 10 characters. And if you happen to be an admin or moderator, we decided the minimum has to be even more, 15 characters.
I also advocated checking passwords against the 100,000 most common passwords. If you look at 10 million passwords from data breaches in 2016, you'll find the top 25 most used passwords are:
123456123456789qwerty1234567811111112345678901234567password123123987654321qwertyuiopmynoob |
12332166666618atcskd2w77777771q2w3e4r6543215555553rjs1la7qegoogle1q2w3e4r5t123qwezxcvbnm1q2w3e |
Even this data betrays some ASCII-centrism. The numbers are the same in any culture I suppose, but I find it hard to believe the average Chinese person will ever choose the passwords "password", "quertyuiop", or "mynoob". So this list has to be customizable, localizable.
(One interesting idea is to search for common shorter password matches inside longer passwords, but I think this would cause too many false positives.)
If you examine the data, this also turns into an argument in favor of password length. Note that only 5 of the top 25 passwords are 10 characters, so if we require 10 character passwords, we've already reduced our exposure to the most common passwords by 80%. I saw this originally when I gathered millions and millions of leaked passwords for Discourse research, then filtered the list down to just those passwords reflecting our new minimum requirement of 10 characters or more.
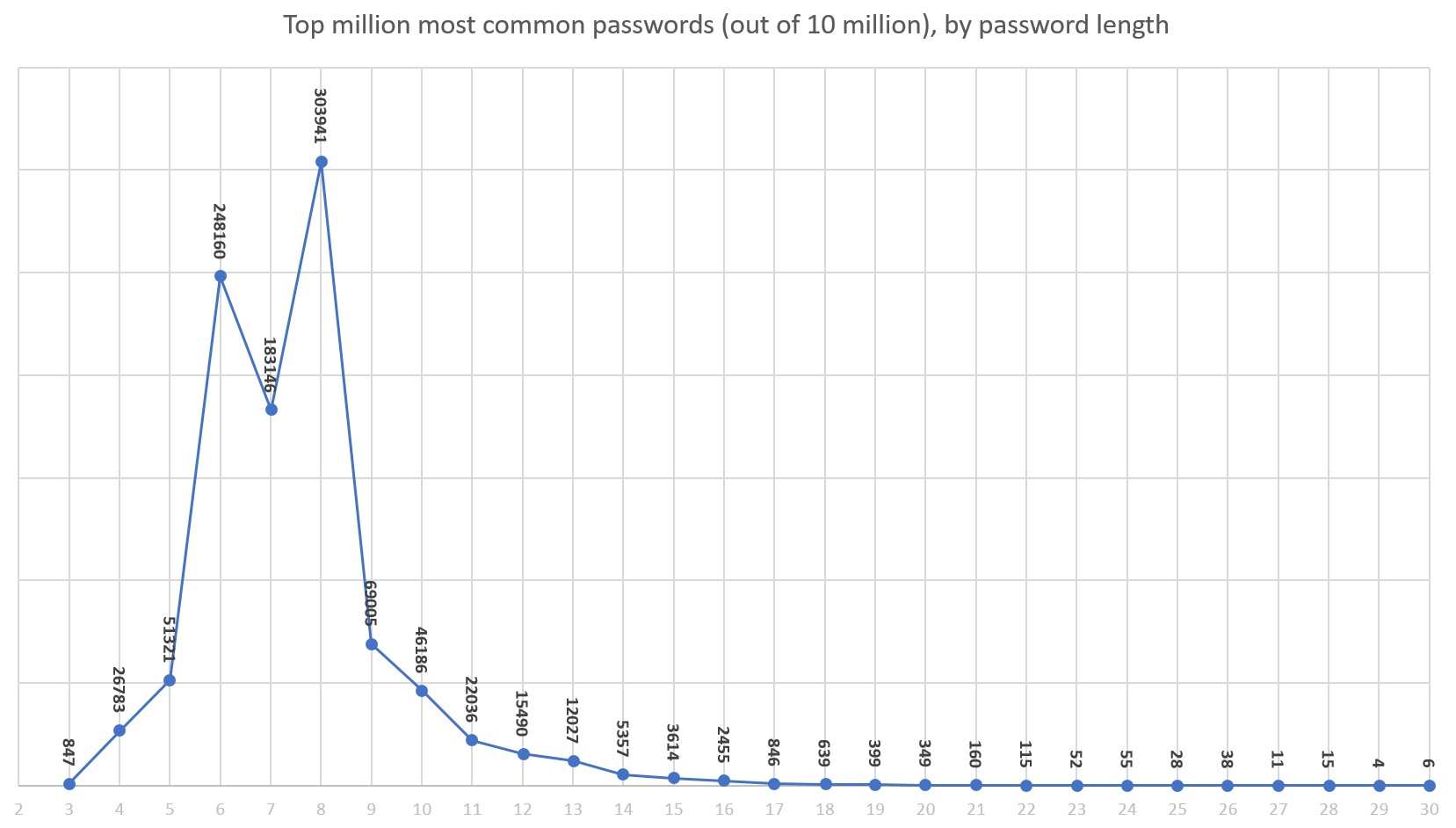
It suddenly became a tiny list. (If you've done similar common password research, please do share your results in the comments.)
I'd like to offer the following common sense advice to my fellow developers:
One rule is at least easy to remember, understand, and enforce. This is the proverbial one rule to bring them all, and in the darkness bind them.

As I've already noted, the definition of "common" depends on your audience, and language, but it is a terrible disservice to users when you let them choose passwords that exist in the list of 10k, 100k, or million most common known passwords from data breaches. There's no question that a hacker will submit these common passwords in a hack attempt – and it's shocking how far you can get, even with aggressive password attempt rate limiting, using just the 1,000 most common passwords.
Lucky you, there are millions and millions of real breached password lists out there to sift through. It is sort of fun to do data forensics, because these aren't hypothetical synthetic Jack the Ripper password rules some bored programmer dreamed up, these are real passwords used by real users.
Do the research. Collect the data. Protect your users from themselves.
No need to get fancy here; pick the measure of entropy that satisfies you deep in the truthiness of your gut. But remember you have to be able to explain it to users when they fail the check, too.
I had a bit of a sad when I realized that we were perfectly fine with users selecting a 10 character password that was literally "aaaaaaaaaa". In my opinion, the simplest way to do this is to ensure that there are at least (x) unique characters out of (y) total characters. And that's what we do as of the current beta version of Discourse. But I'd love your ideas in the comments, too. The simpler and clearer the better!
I'm embarrassed to admit that when building the Discourse login, as I discussed in The God Login, we missed two common cases that you really have to block:
🤦 If you are using Discourse versions earlier than 1.4, I'm so sorry and please upgrade immediately.
Similarly, you might also want to block other special cases like
In short, try to think outside the password input box, like a user would.
🔔 Clarification
A few people have interpreted this post as "all the other password rules are bullshit, except these four I will now list." That's not what I'm trying to say here.
The idea is to focus on the one understandable, simple, practical, works-in-real-life-in-every-situation rule: length. Users can enter (almost) anything, in proper Unicode, provided it's long enough. That's the one rule to bind them all that we need to teach users: length!
Items #3 through #5 are more like genie-special-exception checks, a you can't wish for infinite wishes kind of thing. It doesn't need to be discussed up front because it should be really rare. Yes, you must stop users from having comically bad passwords that equal their username, or
aaaaaaaaaaaor0123456789, but only as post-entry checks, not as rules that need to be explained in advance.So TL;DR: one rule. Length. Enter whatever you want, just make sure it's long enough to be a reasonable password.
| [advertisement] Building out your tech team? Stack Overflow Careers helps you hire from the largest community for programmers on the planet. We built our site with developers like you in mind. |