PHP Frame 2D Class (New)
Read more at https://www.phpclasses.org/package/11832-PHP-Process-structures-of-2D-rigid-joint-frames.html
Latest PECL Releases:
Bug Fixes
Bug Fixes
The post Interview with Miriam Schwab and Zeev Suraski appeared first on Voices of the ElePHPant.
Another monthly update where I explain what happened with Xdebug development in this past month. These will be published on the first Tuesday after the 5th of each month.
Patreon and GitHub supporters will get it earlier, on the first of each month.
I am currently looking for more funding.
You can become a patron or support me through GitHub Sponsors I am currently 59% towards my $1,000 per month goal.
If you are leading a team or company, then it is also possible to support Xdebug through a subscription.
In September, I worked on Xdebug for about 60 hours, with funding being around 70 hours. I worked mostly on the following things:
This month I mostly focussed on getting Xdebug 3 in shape for a first beta release, with all the new configuration names in place. There are now only a few tasks before I can release Xdebug 3.0.0beta1. I plan to release this around PHP 8.0RC2.
The main changes that I made was to rename the following four configuration settings, mostly to get "rid" of the remote naming:
xdebug.remote_host → xdebug.client_host
xdebug.remote_port → xdebug.client_port
xdebug.remote_connect_back → xdebug.discover_client_host
xdebug.remote_addr_header → xdebug.client_discovery_header
I hope that these new names are easier to explain, and of course the upgrade guide explains the changes too.
Although RC1 of PHP 8 is released today, there are still numerous items still in flux. In September there were various changes due to PHP 8's new named parameters. This mostly has an effect on Xdebug's tests, where these names are exposed as part of tracing or debugging tests. Because there are still changes, I am delaying Xdebug 3.0.0beta1 until PHP 8.0RC2.
Other API changes also meant that I had to make changes in Xdebug. Most notably related to code coverage, where PHP 8 will emit fewer Op codes and now (finally!) creates ASSIGN operations on the correct line (which makes Xdebug's breakpoint resolving feature less necessary).
There were two Xdebug releases in September. 2.9.7 changes the step debugger to set up TCP Keepalive probes. This results in better time-out management in case network connections between Xdebug and an IDE drops.
Unfortunately this patch caused compilation issues on FreeBSD where some OS specific flags are different (but the same as OSX, which Xdebug did handle correctly). A fix for this, as well as a fix for path/branch coverage with foreach loops resulted in the 2.9.8 release. I expect to create one more release related to the TCP Keepalive addition as the current release still does not compile for AIX.
Beyond this, I do not expect any more release of the Xdebug 2.9 series unless security or crash bugs are present.
Beyond fixing an off-by-one error in host name generation, I did not write any code for Xdebug Cloud. However, work is ongoing on a web site, and JetBrains is also working on supporting Xdebug Cloud in PhpStorm. Reports state that a prototype is now working. With one IDE soon to support Xdebug Cloud I am also sharing the protocol changes with other IDE/debug client authors before I make it part of the DBGp specification.
Truncated by Planet PHP, read more at the original (another 1282 bytes)
Economies rise and fall. It’s a cycle that can impact all of us in both positive and negative ways. But freelancers can be particularly vulnerable to these shifts.
Working as a solo web designer means that you’re always fending for yourself. Still, an economic downturn makes survival all the more challenging. Things can become precarious before you know it.
It doesn’t have to be all doom and gloom, though. Tough times can actually be a great opportunity to experiment and find (or redefine) your niche.
Whether the economy has your business sputtering or not, it’s important to think about ways you can kickstart growth in your own little corner of the web. And we’re here to help. Today, we’ll offer up some ideas that empower you to do more than just weather the storm.
The head-spinning pace of web development is one way to ensure that we remain essential workers in the online space. Something as (seemingly) simple as your favorite CMS upgrading a JavaScript library can cause all sorts of havoc.
Of course, there are plenty of other examples. Websites running any sort of legacy code are likely going to face incompatibilities at some point. Not to mention that plugins, themes and other tools we rely on don’t last forever.
Proactively looking for these types of issues on your client’s websites can be a solid source of revenue. This is a subject we should be thinking about anyway, as being inattentive to this evolution risks that something will break.
But it’s not just a matter of fixing old code. You might also explore other challenges your clients are facing. Perhaps there was a feature they really could have benefited from that wasn’t feasible a few years ago. Maybe it’s time to revisit the subject?
The main idea is to look for areas to repair or otherwise improve. It’s more than likely you’ll find a few things to keep your business going in the short-term.

Whether you’re already feeling the pinch of a downturn or want to be prepared just in case, it’s a good time to look at your money situation.
The first thing to review is your expenses – especially recurring ones. Are you spending money wisely? Things like web hosting, marketing services or even software licensing may be bleeding your bank account dry. When you have less money coming in, some of these items could be seen as unnecessary.
Now, this doesn’t mean you have to cut out each item completely. There may be some cases where simply downgrading an account level can save you some cash while still providing value.
It’s not always about cutting back, though. This could also be an opportunity to invest in areas that could make you more money now and in the future. Tools or even online educational courses have the potential to do that.
The most important part of this is knowing where you stand. From there, you can make decisions that can have a positive impact on your bottom line.
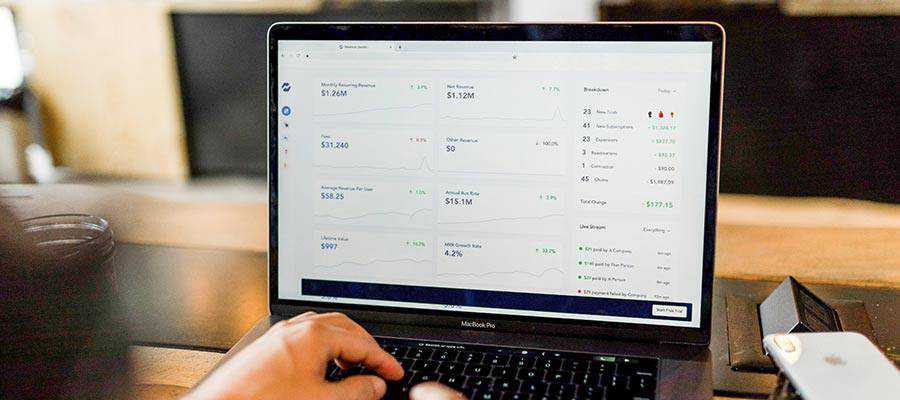
Recurring revenue is something that can carry you through tough times. It’s money you can depend on – bringing at least some level of certainty to your business.
Among the most common ways to gain recurring revenue is to partner up with another firm on a freelance/contract basis. Maybe it’s another freelancer who could use some extra help, or an agency that needs someone within your specialty.
These opportunities may start on a trial basis – which is smart. It’s always best to see what type of synergy the relationship brings. If things work out, you could have a long-term partner that provides a steady stream of income.
Then there is also the possibility of selling a product or service with some recurring revenue. A downturn could be the perfect chance to finally build that app or plugin you’ve been thinking about, or write the eBook that has been rattling around in your head.
What’s more, you can take on these projects in a way that suits your needs. You could, for example, provide regular updates to that app or even spruce up your writing as technology changes. Or, it might simply be a case of bringing in some passive income from your hard work.
Ideally, this will allow you to diversify your earnings. The more reliable sources of money you can procure, the better you’ll be able to maintain economic certainty.

Maintaining patience may just be the hardest thing on this list. Especially so in the face of a downtrodden economy. Yet it is no less vital.
Mind you, we’re not talking about just sitting around, waiting for things to happen. Rather, it’s a matter of carrying out your vision and not wavering in a challenging time.
In practice this means going after the types of clients that are the best fit for you and your business. If you’re looking for a certain sweet spot when it comes to project size and revenue, don’t be afraid to seek out the right opportunity. That is, as long as you can afford to do so.
Avoid settling for projects you don’t want to do – unless it’s an absolute necessity. Otherwise, you may book yourself into a corner and not be able to take advantage when the perfect fit does come along.

A difficult stretch for the economy doesn’t have to be a bad omen for your freelance web design business. While the potential for a negative impact is there, you may not feel the effects nearly as much as a larger business would.
Why is that? Freelancers have a level of flexibility that makes it possible to adjust as needed. So, even losing a big client is something you can recover from. That might not be the case for big companies with physical locations and employees to account for.
It’s an opportunity you need to seize. If something’s not working, change it. Take it upon yourself to be proactive and develop symbiotic relationships with other firms. Help your existing clients up their game.
There are so many ways to keep bringing in much-needed cash. Do it well and you may even find yourself ahead of your previous earnings pace.
Yes, it’s a challenge. But it’s one you can meet head-on.
The post How Freelance Designers Can Thrive in a Tough Economy appeared first on Speckyboy Design Magazine.
Building and securing a WordPress website is always a challenge. Developers take great care to write solid code and implement features such as security plugins to mitigate the inevitable attacks.
Even so, we’re not out of the woods. To paraphrase the old saying: a website is only as secure as its weakest link. Beyond potential exploits due to code, the weakest link tends to be an uninformed user. Someone who, through no fault of their own, makes a bad choice that leaves their website vulnerable.
To use another cliché: the best defense is a good offense. In this case, it means being proactive when it comes to teaching clients about security best practices. Some things (like strong passwords) are universal, while others are a bit more specific to WordPress itself. And that’s our focus for today.
With that, let’s review five things your clients need to know about WordPress security.
We get it: the temptation to install plugins is real. They are, after all, just a few clicks away within the dashboard.
But the risk is also real. WordPress plugins vary greatly in terms of quality and, thus, security. It’s not uncommon to find a plugin in the official repository that hasn’t been updated in a year or more. Maybe it’s harmless, maybe it’s not.
Because of this, web designers should encourage clients to perform a quick consultation before installing a plugin. Offer to take a look and review the particulars. This single step could prevent a nightmare scenario with regards to security and site stability.
There are a number of benefits. First, this keeps you in the loop as to what’s going on with the site. In addition, it gives you the opportunity to point clients in the direction of good, reputable plugins. Not to mention that this trains clients to think before they click. That benefits everyone.
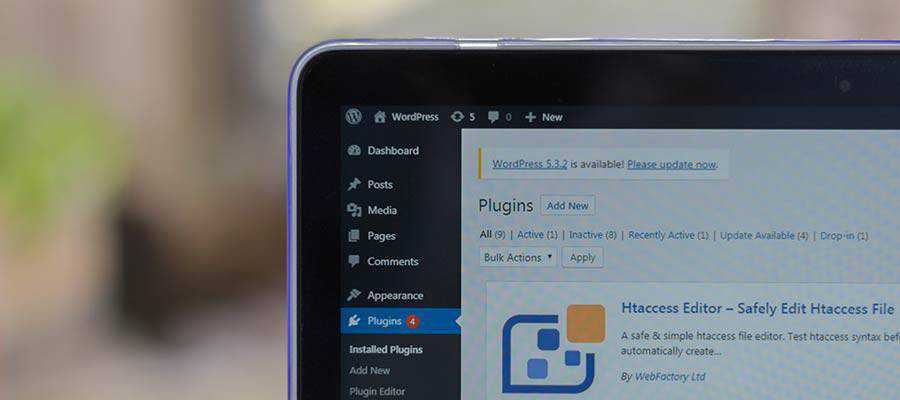
Many organizations have more than one person who needs access to the WordPress dashboard. Too often, those users share a single account.
On the surface, this may seem like a simple matter of trust. And there certainly is an element of that. If a team member leaves the organization, there is the possibility of them still having access if the password hasn’t been changed. And a malicious person could do some damage.
The other real concern here is about device security. If you have, say, five people sharing a WordPress administrator account, all it takes is one of their devices to be exploited. For example, a keylogger on one user’s PC could compromise the account.
Therefore, it’s recommended that each user have their own account. This is easy to do within WordPress, and we can even create custom user roles that limit what someone can and can’t do.

Ideally, your clients will contract with you to handle software updates. But if they’re the ones taking responsibility, it’s important that they treat the issue very seriously.
As a developer, there are few things more irritating than troubleshooting a compromised website, only to log into WordPress and see that things are several versions out-of-date. It’s akin to leaving the front door of your house wide open, 24/7. You shouldn’t be too surprised when someone comes in and takes your fancy new TV.
The importance of keeping WordPress core, plugins and themes updated cannot be overstated. Knowing that, it still may be beyond the comfort level of some clients. That’s OK. Either they can hire you to deal with it or, at the very least, enable auto updates where possible.
Regardless of how updates are implemented, it’s vital that they’re taken care of. While it won’t guarantee security, it’s much better than the alternative.

Adding two-factor authentication to WordPress is fairly simple. But it’s only worthwhile if stakeholders actually use it.
True, it’s not very convenient. Having to verify an email, a text message or check a mobile app to login can be a major pain. But this extra step is vital. It puts up a huge barrier between a malicious actor and access to your website’s back end.
And the user experience is actually getting better. Some implementations are now combining device recognition with 2FA. This means that, so long as a user’s device is recognized, there won’t be a need to verify a login for a specified amount of time.
Plus, 2FA has become standard in so many places. Some online banking apps won’t let you login without it. There’s no reason why your website shouldn’t take advantage of this technology as well.

Regardless of the platform it runs on, a website is not a one-and-done affair. It requires frequent (if not constant) attention – with security playing a major role.
The web is constantly evolving. New technology gets old very quickly. And what was once thought to be a security best practice can sometimes be proven otherwise.
Because of that, website security is a challenge that really has no end. It’s a daily battle for small and large organizations alike.
The result is that websites need to change along with the times. When it comes to WordPress, that may mean replacing older security plugins with something better. Or doing away with abandoned themes and plugins in order to tighten things up. It could also require a change in hosts or server environments.
It’s important to understand that, just because you’ve invested in security today, doesn’t mean you won’t have to do so again tomorrow.

Our clients often rely on us to provide some knowledge along with a killer website. And security may just be the most important subject we can educate them on.
Making the effort to do so from the beginning can pay long-term dividends. A client who understands how to keep their WordPress website secure is less likely to make one of those crucial mistakes. That alone may be the difference between cleaning up a hacked site and smooth sailing.
The post 5 Things to Tell Your Clients About WordPress Security appeared first on Speckyboy Design Magazine.